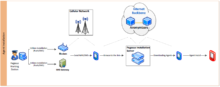
In August 2016, Citizen Lab released a report uncovering how United Arab Emirates (UAE) activist Ahmed Mansoor was targeted with “Pegasus” (sophisticated government-exclusive spyware) and “The Trident” (a chain of iOS zero day exploits) designed to infect his iPhone 6 via a malicious link in an SMS text message. They attributed Pegasus and The Trident exploit chain to an Israel-based “cyber warfare” company, NSO Group.
In February 2017 Citizen Lab, with assistance of Mexican non-governmental organizations (NGOs) R3D and SocialTic, documented how Mexican government food scientists, health, and consumer advocates also received links to infrastructure that researchers connected to NSO Group. They suspect that the links were designed to install Pegasus on their phones.
This report expands the Mexican investigation and shows how 10 Mexican journalists and human rights defenders, one minor child, and one United States citizen, were targeted with NSO’s Exploit Framework.
Read blog post by Ron Deibert.
Follow this research in the news
Using texts as lures, government spyware targets Mexican journalists and their families (New York Times)
This report says the Mexican government deployed spyware against journalists and activists (Buzzfeed)
Mexican journalists, activists targeted with spyware (Washington Post)
Report: Mexican journalists, activists targeted with spyware (Financial Post)
Mexico’s Sloppy Hacking Attempts Expose Customers of a $1 Billion Spyware Company (Motherboard)
Report: Mexican journalists, activists targeted with spyware (ABC News)
Mexican journalists targeted by spyware after investigating government corruption (The Verge)
Fake evidence of affairs and other creepy ways government spyware is targeting Mexican journalists (Quartz)
Mexico to Investigate Spying Campaign Against Journalists and Activists (New York Times)
Mexico probes spyware attacks on journalists, activists (National Post)