Cybersecurity and civil society
Spyware infecting our phones. Endless hacks and cyber-attacks. Censored online conversations. Counterfeit tweets and posts. Personal data misused – or stolen and sold to the highest bidder. We’ve embraced the convenience and opportunity of a digitally connected world. But we also feel increasingly vulnerable, as criminal hackers and political manipulators leverage our private information and opinions to further their ends. The extraordinary digital technology that’s bringing the world closer together also threatens to split us apart.

Supporters around the world held protests, including this one in London, England, demanding the release of Noura Al-Jizawi and other women being detained in Syria.
Photo: Courtesy of Freedom For Activist Noura Aljizawi Facebook page.
“For the future of Syria, we won’t need only activism experience. We need academic experience. We need to be thinking about innovative development strategies for a country destroyed totally – buildings, institutions and humans.”

Noura Al-Jizawi with her three-month-old baby, Naya. Al-Jizawi joined U of T’s master’s program at the Munk School of Global Affairs last year through a Scholars at Risk scholarship.
Photo: Noreen Ahmed-Ullah.
Noura Al-Jizawi
Like many MGA students at the Munk School, Noura Al-Jizawi has a keen interest in the Syrian conflict and its global consequences. But she also has a unique first-hand perspective – as a young activist who helped ignite the civil uprising against the regime of President Bashar al-Assad, and who went on to become one of the leaders of the opposition in exile.
What began as a peaceful revolt in 2011 escalated into a full-scale civil war that has left more than 465,000 Syrians dead and over 12 million displaced. In the early years, Al-Jizawi wrote a pro-democracy blog, organized protests, posted photos of victims – many of them close friends killed by the regime – and travelled around Syria mobilizing others. She was detained several times and tortured by her jailers. Several of her family members were also arrested and beaten. It was too dangerous to stay any longer: she began planning her escape to Turkey.
What followed was a gruelling 20-day journey. Al-Jizawi travelled mainly on foot, waded across rivers and rode donkeys through mountain passes. Once safely across the Turkish border, she immediately started an NGO to help victims of torture and female survivors, and to advocate on behalf of those who’d been forced to abandon their homeland. She also became a vice-president of the Syrian opposition – one of the few women in the coalition of leaders who would ultimately sit down across from Assad’s negotiating team.
Al-Jizawi first encountered the Munk School of Global Affairs in 2014, when her email account was targeted by a cyber-attack. The Citizen Lab came to her aid, analyzing the virus and reporting on what was clearly a sophisticated spyware campaign against the Syrian opposition. A bond was forged, and when Al-Jizawi decided to resume her studies at graduate school, the only option she considered was an MGA at the Munk School. She joins a growing number of human rights activists who’ve been welcomed into the University of Toronto community through the Citizen Lab. Supported by the University’s Scholars at Risk program, she is also the 2017–2018 recipient of the Paul Cadario Fellowship in Global Affairs, which is awarded to a promising first-year MGA student based on merit and need.
In February 2018, Al-Jizawi attended the 37th Session of the United Nations Human Rights Council in Geneva. Sharing her experience of forced migration in Syria, she urged that the rights of refugees and internally displaced people be upheld in any future negotiations with the Assad government. Now back in Toronto to complete her studies (and raise her newborn daughter), Al-Jizawi remains hopeful for the future and is focused on how she can contribute to rebuilding her country when the conflict finally ends. Completing her MGA and strengthening the network she’s built at the Munk School are important steps in that journey.
Reckless Exploits
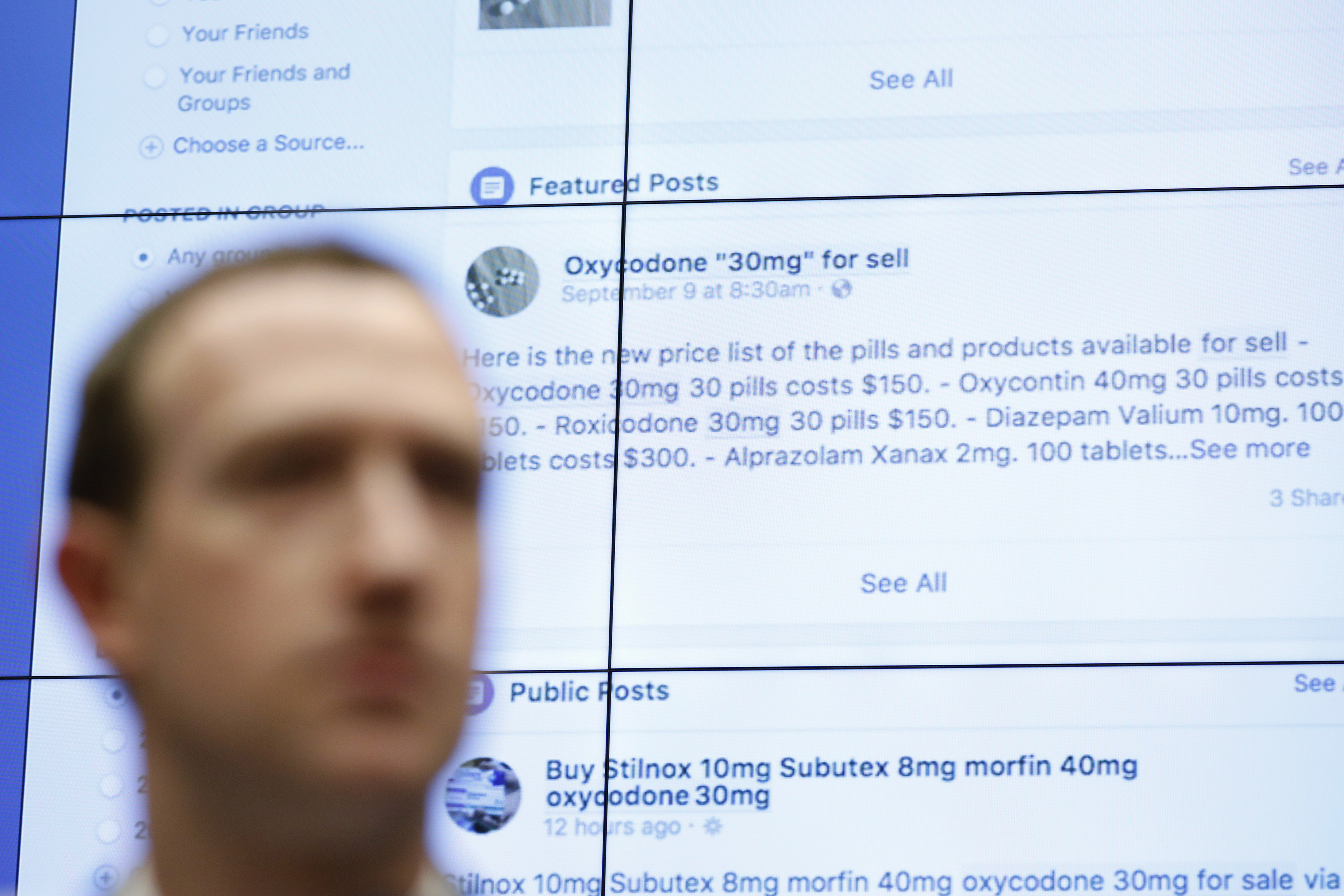
Imagine if someone could remotely access everything on your smartphone: private calls, emails, texts, appointments – even the built-in camera and microphone. In 2017, a cybersecurity investigation in Mexico detected attempts to plant this kind of invasive software on the phones of several prominent journalists, lawyers and activists, all of them known to be examining aspects of political and police corruption. Even more troubling: the spyware used to target them is sold exclusively to governments, with the explicit assurance that it will only be used to combat threats to public safety.
This cybersecurity attack was exposed by the Citizen Lab, the Munk School research hub that brings together experts in political science, law, computer science and area studies. The Citizen Lab has earned a global reputation for research and policy work at the intersection of technology, human rights and security. In a series of reports titled Reckless Exploits – referring to “zero-day exploits” that attack previously unknown vulnerabilities in software or hardware – the Citizen Lab has shown how technology meant to support law enforcement has been inappropriately deployed: “Spyware sold to governments ostensibly to track terrorists and investigate criminals is, in a growing number of documented incidents, abused for nakedly political ends.”
In the Mexican cases, digital surveillance software sold by Israel-based NSO Group was used to infect the phones of two lawyers who’ve investigated many high-profile cases, including the execution-style killing of several human rights activists. The spyware, called Pegasus, was also used to target a group of international experts investigating the 2014 disappearance of 43 male students, apparently after they were abducted by corrupt police in the city of Iguala.
Some of the messages used to trick unwitting recipients appeared to come from the U.S. Embassy in Mexico, while others were disguised as Amber Alerts about abducted children. At least one was directed at a minor: the teenaged son of an adult target received a counterfeit message from authorities in Washington while visiting the U.S. The Citizen Lab team also detected a cyber-attack against an American who advocates for victims of sexual abuse by the Mexican police.
NSO Group maintains its “cyberwarfare” products are sold to government agencies with stringent agreements restricting their use to legitimate security efforts. In Mexico, the spyware was supposedly acquired as a weapon in the battle against the drug cartels and criminal gangs that have long terrorized the country. But the work of the Citizen Lab, detailed in a series of online reports, makes clear that those agreements are not being respected.
The Reckless Exploits initiative has fuelled front-page stories in The New York Times and extensive coverage by media outlets worldwide. Questions it raises about the potential abuse of surveillance technology have been discussed in the U.S. Congress and at the State Department. The work continues – in Mexico and beyond – amid growing concern that mobile devices, while empowering to many communities, may also provide a means of disrupting civil society.
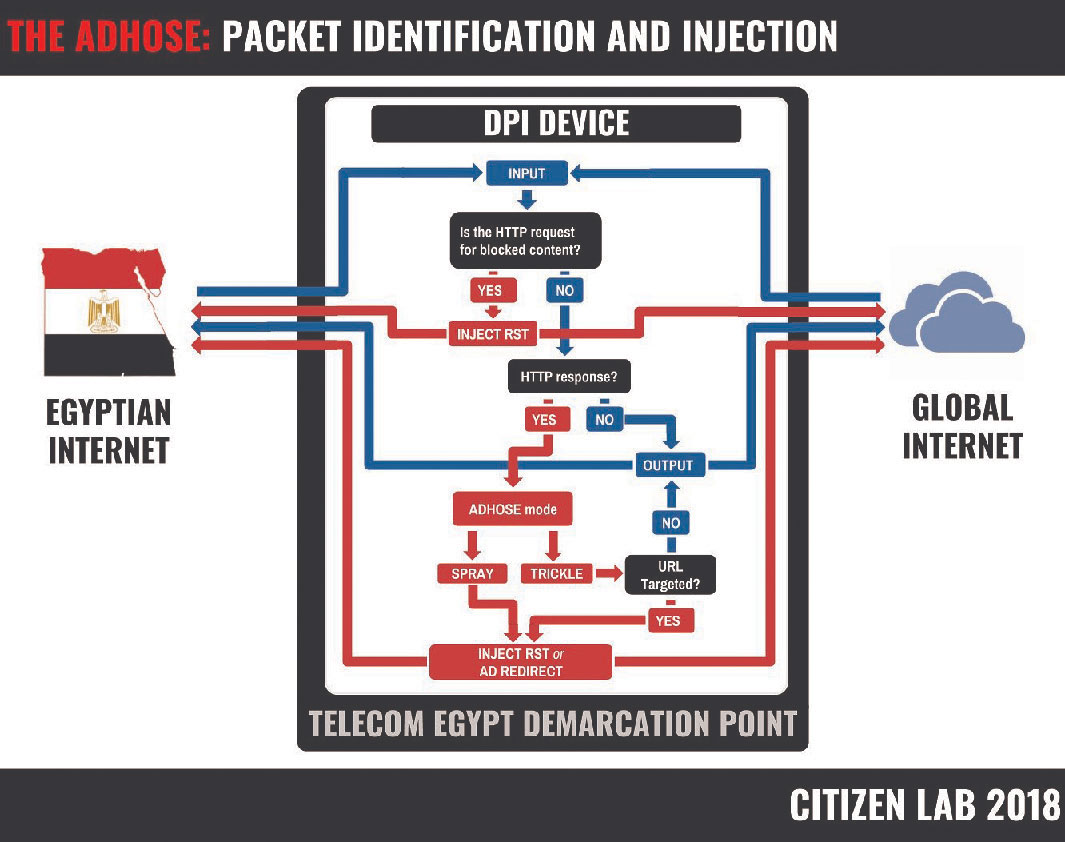
Illustration: The Citizen Lab.
Bad Traffic
As more and more information travels over highly accessible global networks, we’ve all learned to be cautious about the data we allow onto our devices. But sometimes threats are built right into the networking technology.
In the past year, the Citizen Lab reported that equipment on a Turkish telecom network was being used to install spyware on the devices of people trying to download legitimate Windows applications. Traffic-handling “middleboxes,” provided by a company based in the U.S. and Canada, had prompted users in Turkey and Syria to unwittingly install software capable of censoring web content. It directed them to revenue-generating sites or linking their computers to others in invisible – and profitable – cryptocurrency mining operations. Citizen Lab experts found similar middleboxes on the Telecom Egypt network that were apparently being used to hijack users’ unencrypted web connections en masse, sending them to sites where they could be misled into sharing data or paying for questionable transactions.
“Leaked documents have long indicated that a number of governments are targeting their opponents by surreptitiously injecting spyware into their internet connections,” Citizen Lab researcher Bill Marczak told U of T News. “For the first time ever, we have the proof.”
For Prof. Ron Deibert, director of the Citizen Lab, the discovery of abuses in one region underlines the need for greater vigilance globally: “Targeted injection of spyware at the nation-state level represents a major public safety risk, and technologies that facilitate such injection should be regulated accordingly. The apparent use of [middleboxes] to surreptitiously inject malicious and dubious redirects for users in Turkey, Syria and Egypt raises significant human rights concerns.”